When logging in to a computer account or to services online, known as the ‘authentication process,’ we all provide information that theoretically proves our identity. Traditionally, this verification has relied on a combination of a username (often an email address) and a password; together these are known as ‘user credentials’. However, ‘theoretically’ is the key word because this approach is not particularly secure and there are now more effective measures we can, and should, take.
This is where multi-factor authentication (MFA) comes in.
Why a username and password is not enough
If we use our email address as our username, it can become widely known on the internet. And while this makes it easier for people to contact us, it also makes it easy for others to find. It may also end up in various contact lists or even on a company website.
Other types of usernames are easily deduced by considering a company name, or other publicly available details, such as your surname. It is quite common to see email addresses such as J.Smith@Company.com. So, it is a trivial matter for a hacker to create lots of possible usernames to try out, for example, johnsmith or smithj123, which means that half of the defence against someone else pretending to be you or me and logging in, in our name, may already be beaten.
So, what about passwords?
We all have many things to remember, so as fallible humans, we tend to choose simple passwords. Unfortunately, these are too easy to crack. Or people choose one that can be easily remembered, and these are, therefore, quite easy to research and find. For example, they might use a favourite pet’s name but then they have pictures and the name of that pet on their Facebook page. Or we might have a more complicated password but reuse it for lots of different purposes, maybe for work, a webmail account, and several online shopping accounts – so having it exposed once leads to the risk of compromise for all of those accounts. So, passwords are imperfect and given the computing power available to guess or crack them these days, not a particularly strong defence either.
Finally, after many years of data breaches and ransomware attacks affecting companies worldwide, it is now highly likely that most people have had at least one set of their credentials stolen. These are published on the Dark Web and available for hackers to buy. So, despite using stricter password policies, or complicated usernames, in many cases, cyber criminals can easily access your accounts by using the legitimate credentials they have bought.
They don’t have to ‘hack’ in, they just log in.
You can check if your email address has been in a data breach.
Cue Multi-Factor Authentication (MFA)…
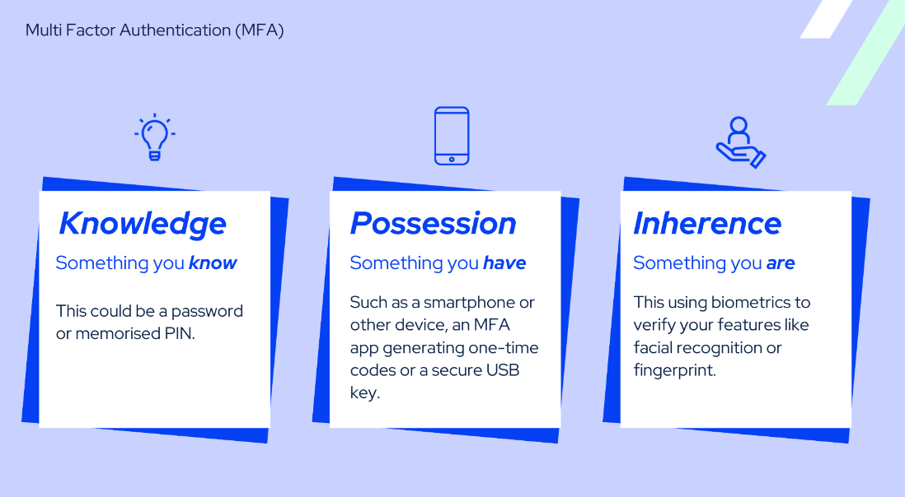
One solution to the above problem is to rely on more than just a username and password by adding to the overall challenge of proving your identity, for example, using additional information about something you are, something you know or something you have. These distinct characteristics can be used to determine if someone is logging in as you, or really is you. Because these are additional identification factors, in shorthand, this is Multi-Factor Authentication (MFA).
MFA requires users to provide multiple forms of identification or separate verification to access a system or an account. In other words, it makes you prove your identity in multiple ways, not just with a username and password, they need another piece of the puzzle to get in. It's like having a secret code, a physical key, and maybe even your fingerprint, all working together to keep your sensitive online information safe.
For many of us, this has become commonplace as many online services, for example, banking apps, have already added MFA as an essential step when logging in. The process will usually go something like this:
1. You initially log in with your username or email and a password.
2. It will then check the device you are using to see if it recognises it as being registered (so it's something you have)
3. Or it may send a prompt to you to;
a. Input a code to another device, or account (something you know)
b. Activate the option to use Face ID to verify you (something you are)
c. Use an authenticator app to generate a one-time code for you to use (something you have).
This is all MFA is – it just means using additional ‘factors’ to check it really is you using your credentials, not someone else.
Why is MFA now essential?
Unfortunately, as mentioned above, it is quite easy it is to obtain user credentials, and once they are compromised this poses a plethora of onward risks for both users and businesses. A traditional password and username combination is just no longer good enough security. By enabling and using MFA, we can increase the security of our accounts, reduce the risk of unauthorised access, and provide an additional layer of protection against various cyber threats.
In summary, MFA can provide:
Enhanced Security: MFA’s multi-layered approach significantly reduces the risk of unauthorised access, as even if one factor is compromised, the attacker would still need access to the other factor(s) to gain entry.
Cost saving: Enabling MFA is not expensive; the necessary technology is usually bundled for free with modern IT systems. Compare this to the cost of a data breach or ransomware attack which might be measured in fines or losses of several tens or hundreds of thousands of pounds, or even just a sizeable percentage increase in annual cyber insurance premiums. Having these simple precautions implemented in daily practice makes the few extra seconds it may take everyone to log in, very much worth it.
Mitigation of Stolen or Lost Credentials: MFA helps mitigate the risk associated with stolen or lost credentials. If a user's password is compromised, for example, if they click on a link in a phishing email, the unauthorised person who gains their details would still need an additional factor (e.g., their physical device or biometric data) to authenticate successfully. This adds an extra layer of protection, reducing the impact of credential theft or loss.
Compliance Requirements: Many industries and regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR), require organisations to implement MFA as part of their security measures. Adhering to these compliance standards helps protect sensitive data, ensures an organisation meets its legal obligations and is attractive to your customers.
Remote Workforce and Cloud Services: With the rise of remote work and cloud-based services, the traditional perimeter-based security model is no longer sufficient because people no longer only use a work computer in a controlled location. MFA adds additional security that enables remote access to corporate networks, cloud applications, and sensitive data.
User-Friendly Experience: MFA solutions have evolved to be user-friendly, offering convenient options such as push notifications or biometric authentication. This ensures that the user experience is not significantly disrupted while security is enhanced.
Overall, the benefits of increased security massively outweigh the small inconvenience of an extra authentication step.
Is MFA bulletproof?
No, but nothing in computing technology is. However, not having MFA means taking a much greater and unnecessary level of cyber security risk. Some of the issues with MFA are described below for transparency but the best defence against all of these is staff training and new policies should be considered in this instance, especially if you haven’t implemented MFA before:
MFA fatigue attacks: An individual is subject to an ‘MFA fatigue attack’ when they receive lots of prompts to input an authentication code when they haven't requested it. This provokes confusion and annoyance, encouraging the individual to eventually accept a prompt which is not legitimate. As always, users should be healthily suspicious when unexpected actions are requested by their device.
Device compromise: If a user's trusted device or MFA token is compromised or stolen, attackers may be able to gain the additional ‘something you have’ factor and obtain account access. Ensuring devices are treated with care, backed up and can be remotely disabled, plus encouraging an open reporting culture among staff, are good precautionary measures to alleviate this risk.
Backup authentication methods: Many MFA systems offer backup methods for users to access their accounts in case the primary factor is unavailable. If these backup methods are not adequately secured, they could become a target for attackers. However, managed IT and cyber security service providers can efficiently set up, store, and manage backups like this to address these risks.
Emerging attack techniques: As security measures evolve, attackers may develop new techniques and strategies to circumvent MFA. This requires continuous monitoring and updates to stay ahead of emerging threats.
While MFA significantly raises the bar for attackers and makes unauthorised access more challenging, it is important to approach it as one component of a comprehensive security strategy. It should be combined with other security measures, such as robust password/passphrase policies, regular security updates and employee education, to create a more resilient security posture for your business. Bluecube offers a managed cyber security service and monitoring for this reason, to ensure you can always stay ahead of the curve.
How can MFA be managed to work seamlessly and securely, for you?
We know having another thing set up could be a pain, but the traditional approach of passwords and usernames is simply outclassed by modern cyber-attack methods. MFA is now an almost essential security layer (there are some very specific and few circumstances where it is impractical) and there are ways to make it manageable for you and your business. It is generally easy to set up and maintain, and most people in your business are already familiar with using it, whether they know it or not.
For some businesses, it may be easier to have MFA managed by an IT/cyber security provider. This is because each employee in the business will be accessing a variety of systems, accounts and devices that will all need MFA activated on them. They are also able to provide instruction, support, and guidance on the best practices and how to best manage them to work for you.
Increasingly online sites, systems and devices are making MFA requirements, and this too can be hard to keep up with, so handing this over to a service provider like Bluecube can ease the hassle. As well as this, Bluecube are an MSSP that can mitigate the risks through monitoring and providing cyber security services to protect your business from any potential cyber threats including credential theft and MFA fatigue attacks.







