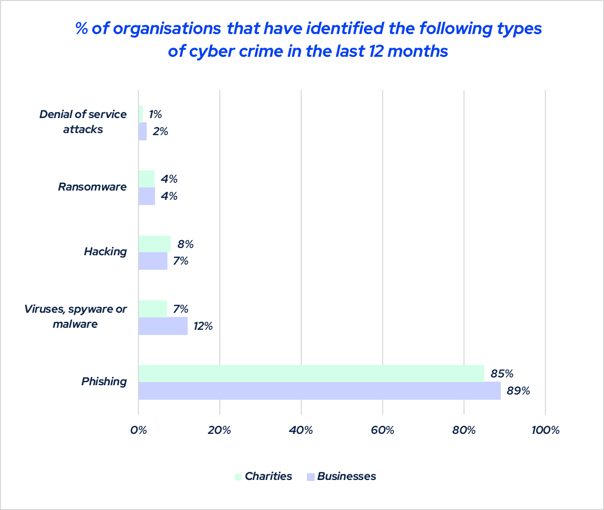
Phishing is a scam tactic that criminals use to steal user data by either installing malware or tricking them into handing over sensitive information. Cyber criminals are finding new ways to do this, but the most common ways they can trick people is by getting individuals to click on a link, images, or attachments or, by convincing them to hand over information by pretending to be a trusted person or organisation.
Login credentials, card details, and sensitive data are all targets of phishing scams. One of the most common methods malicious cyber criminals use is phishing emails that appear to be from a trusted source.
All it takes is one unsuspecting victim to click on a link and they can endanger their company’s security, their friends and family's data, or put themselves at risk of identity theft.
.png)
-1.png)
-1.png)