IT security is not as simple as it used to be.
Nowadays, we see cyber security threats every day.
The cyber threats and number of cyber attacks on businesses are rapidly growing year-on-year. And they are becoming more sophisticated. The risk for businesses is very real. Have you built your cyber resilience?
The changing landscape of cyber-attacks
Gone are the days when a virus writer was creating viruses for “fun", political or anti-establishment reasons – nowadays, it is a big business; whether people are paying to decrypt their data or if they have sent money to a fraudster – and this happens every day.
Technology and software can be used to minimise the risk – but the risk can never be eradicated, mainly due to human behaviours and social engineering. This is how the majority of the bigger frauds are instigated.
Frauds are instigated by criminals, but normally the victim helps them. Before acting, think about what someone is asking you to do.
If you are being asked to click on a link, open a file, send money, verify information... STOP AND THINK.
Below is a video that was released by Cifas (the UKs leading fraud prevention service). The video highlights how much information we share online – all of which can be used to steal our identity or defraud us.

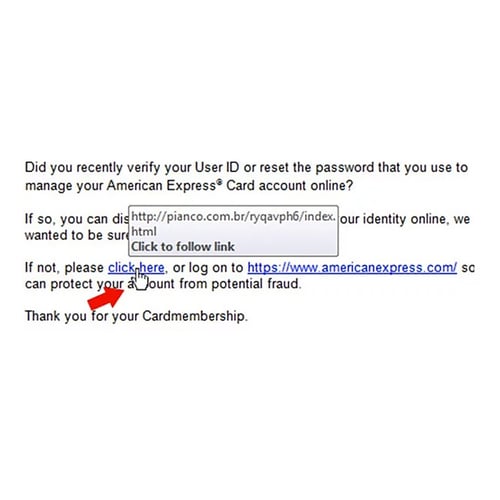 If you are not expecting an email from someone with a link... do not click on it.
If you are not expecting an email from someone with a link... do not click on it. 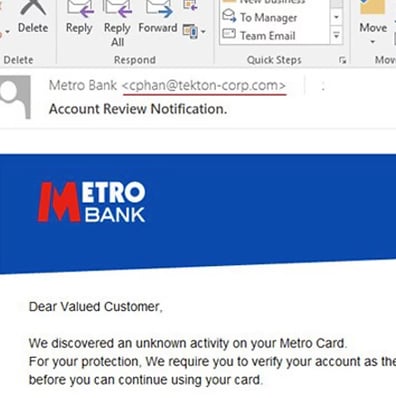 You can usually tell whether the email sender's address is real because of the domain name they use.
You can usually tell whether the email sender's address is real because of the domain name they use.






